All material on this website is protected by copyright, This website also contains material copyrighted by 3rd parties.
 Covert Operations disegnalato da Associazione italiana, scientifica e giuridica, contro gli abusi mentali, fisici e tecnologici è distribuito con Licenza Creative Commons Attribuzione - Non commerciale - Condividi allo stesso modo 4.0 Internazionale.  13 agosto 2016 / August 13 2016 Covert
Operations
|
|
A lawsuit
filed against the U.S. National
Security
Agency reveals a frightening array of technologies and programs
designed to keep tabs on individuals. |
1. THE NSA’S MISSION AND DOMESTIC INTELLIGENCE OPERATION
Communications
Intelligence (COMINT)
Signals Intelligence ( SIGINT)
The Signals Intelligence mission of the NSA has evolved into a program of decoding EMF waves in the environment for wirelessly tapping into computers and track persons with the electrical currents in their bodies. Signals Intelligence is based on fact that everything in the environment with an electric current in it has a magnetic flux around it which gives off EMF waves. The NSA/DoD [Department of Defense] developed proprietary advanced digital equipment which can remotely analyze all objects whether manmade or organic, that have electrical activity.
Domestic Intelligence ( DOMINT)
The NSA has records on all US citizens. The NSA gathers information on US citizen who might be of interest to any of the over 50,000 NSA agents (HUMINT). These agents are authorized by executive order to spy on anyone. The NSA has a permanent national security anti-terrorist surveillance network in place. This surveillance network is completely disguised and hidden from the public.
Tracking individuals in the US is easily and cost-effectively
implemented with NSA’s electronic surveillance network. This network (DOMINT)
covers the entire US, involves tens of thousands of NSA personnel, and
tracks millions of persons simultaneously. Cost-effective
implementation of operations is assured by NSA computer technology
designed to minimize operations costs. NSA personnel serve in
quasi-public positions in their communities and run cover businesses
and legitimate businesses that can inform the intelligence community of
persons they would want to track. NSA personnel in
the
community usually have cover identities such as social workers, lawyers
and business owners.
Individual Citizens Occasionally Targeted for Surveillance
by Independently Operating NSA
Personnel
NSA personnel can control the lives of
hundreds of
thousands of individuals in the US by using the NSA’s domestic
intelligence network and cover businesses. The operations independently
run by them can sometimes go beyond the bounds of law. Long-term
control and sabotage of tens of thousands of unwitting citizens by NSA
operatives is likely to happen. NSA DOMINT has the
ability to
assassinate US citizens covertly or run covert psychological control
operations to cause subjects to be diagnosed with ill mental health.
The
above symptoms highlight a fraction of the vast array of
Neuro-Electromagnetic Frequency Assaults perpetuated by the Police and
Military Intelligence Agencies toward
Remote Mind Control Experiments, Behavioural Manipulation and
Murder.
2. NSA’S
DOMESTIC ELECTRONIC SURVEILLANCE NETWORK
As
of the
early 1960s, the most advanced computers in the world were at
the NSA, Ft Meade. Research breakthroughs with these computers were
kept for the NSA. At the present time the NSA has
nanotechnology computers that are 15 years ahead of present computer
technology. The NSA obtains blanket coverage of information in the US
by using advanced computers that use artificial intelligence to screen
all communications, regardless of medium, for key words that should be
brought to the attention of NSA agents/cryptologists. These
computers monitor all communications at the transmitting and receiving
ends. This blanket coverage of the US is a result of the NSA’s Signals
Intelligence (SIGINT) mission. The NSA’s
electronic
surveillance network is based on a cellular arrangement of devices that
can monitor the entire EMF spectrum. This equipment was developed,
implemented and kept secret in the same manner as other electronic
warfare programs.
Signals Intelligence Remote Computer Tampering
The NSA keeps
track of all PCs and other computers
sold in the
US. This is an integral part of the Domestic Intelligence network. The
NSA’s EMF equipment can tune in RF emissions from personal computer
circuit boards (while filtering out emissions from monitors and power
sup- plies). The RF emission from PC circuit boards contains digital
information in the PC. Coded RF waves from the NSA’s equipment can
resonate PC circuits and change data in the PCs. Thus the NSA can gain
wireless modem-style entry into any computer in the country for
surveillance or anti-terrorist electronic warfare.
Detecting EMF Fields in Humans for Surveillance
A subject’s bioelectric field can be remotely detected, so
subjects can
be monitored anywhere they are. With special EMF equipment NSA
cryptologists can remotely read evoked potentials (from
EEGs).
These can be decoded into a person’s brain-states and thoughts. The
subject is then perfectly monitored from a distance. NSA
personnel can dial up any individual in the country on the Signals
Intelligence EMF scanning network and the NSA’s computers will then
pinpoint and track that person 24 hours a day. The NSA can pick out and
track anyone in the US.

3. NSA
SIGNALS INTELLIGENCE USE OF EMF BRAIN
STIMULATION
NSA
Signals Intelligence uses EMF Brain Stimulation
for Remote Neural Monitoring (RNM)
and Electronic
Brain Link (EBL). EMF Brain Stimulation
has been in
development since the MKULTRA program of the early 1950s, which
included neurological research into radiation (non-ionizing EMF) and
bioelectric research and development. The resulting secret technology
is categorized at the National Security Archives as "Radiation
Intelligence", defined as "information from unintentionally emanated
electromagnetic waves in the environment, not including radioactivity
or nuclear detonation". Signals Intelligence implemented and kept this
technology secret in the same manner as other electronic warfare
programs of the US Government. The NSA monitors
available
information about this technology and withholds scientific research
from the public. There are also international intelligence agreements
to keep this technology secret.
The NSA has proprietary electronic equipment that analyze electrical
activity in humans from a distance. NSA computer generated brain
mapping can continuously monitor all of the electrical activity in the
brain continuously. The NSA records and decode individual brain maps
(of hundreds of thousands of persons) for national security purposes.
EMF Brain Stimulation is also secretly used by the military for
brain-to-computer link (in military fighter aircraft, for example).
For electronic surveillance purposes, electrical activity in the speech
center of the brain can be translated into the subject’s verbal
thoughts. RNM can send encoded signals to the brain’s auditory cortex,
thus allowing audio communications direct to the brain (bypassing the
ears). NSA operatives can use this covertly to debilitate subjects by
simulating auditory hallucinations characteristic of paranoid
schizophrenia.
Without any contact with the subject, Remote
Neural
Monitoring
can map out electrical activity from the visual cortex of a subject’s
brain and show images from the subject’s brain on a video monitor. NSA
operatives see what the surveillance subject’s eyes are seeing. Visual
memory can also be seen. RNM can send images direct
to the
visual cortex, bypassing the eyes and optic nerves. NSA operatives can
use this surreptitiously to put images into a surveillance subject’s
brain while they are in REM sleep for brain-programming purposes.
Capabilities of NSA Operatives Using RNM
There has been a Signals Intelligence
network in
the US since
the 1940s. The NSA, Ft Meade has in place a vast
two-way
wireless RNM system which is used to track subjects
and
non-invasively monitor audio-visual information in their brains. This
is all done with no physical contact with the subject. RNM is the
ultimate method of surveillance and domestic intelligence. Speech, 3D
sound and subliminal audio can be sent to the auditory cortex of the
subject’s brain (bypassing the ears), and images can be sent into the
visual cortex. RNM can alter a subject’s perceptions, moods and motor
control.
Speech cortex/auditory cortex link has become the ultimate
communications system for the intelligence community. RNM
allows for a complete audio-visual brain-to-brain link or
brain-to-computer link.

The
above is a simple flowchart of Neuro-Electromagnetic Frequency Assaults
showing methods that can be perpetuated by the Police and Military
Intelligence Agencies toward
Remote Mind Control Experiments, Behavioural Manipulation and
Murder.
4. NATIONAL
SECURITY AGENCY SIGNALS INTELLIGENCE ELECTRONIC BRAIN LINK TECHNOLOGY
The NSA’s Signals Intelligence has the proprietary ability to monitor remotely and non-invasively information in the human brain by digitally decoding the evoked potentials in the 30-50 Hz, 5 milliwatt electromagnetic emissions from the brain.
Neuronal activity in the brain creates a shifting electrical pattern that has a shifting magnetic flux. This magnetic flux puts out a constant 30-50 Hz, 5 milliwatt electromagnetic (EMF) wave. Contained in the electromagnetic emission from the brain are spikes and patterns called "evoked potentials". Every thought, reaction, motor command, auditory event and visual image in the brain has a corresponding "evoked potential" or set of "evoked potentials". The EMF emission from the brain can be decoded into the current thoughts, images and sounds in the subject’s brain.
NSA SIGINT uses EMF-transmitted Brain Stimulation as a communications system to transmit information (as well as nervous system messages) to intelligence agents and also to transmit to the brains of covert operations subjects (on a non-perceptible level).
EMF Brain Stimulation works by sending a complexly coded and pulsed electromagnetic signal to trigger evoked potentials (events) in the brain, thereby forming sound and visual images in the brain’s neural circuits. EMF Brain Stimulation can also change a person’s brain-states and affect motor control.
Two-way electronic Brain Link is done by remotely monitoring neural audio-visual information while transmitting sound to the auditory cortex (bypassing the ears) and transmitting faint images to the visual cortex (bypassing the optic nerves and eyes). The images appear as floating 2D screens in the brain.
Two-way electronic Brain Link has become the ultimate communications system for CIA/NSA personnel. Remote neural monitoring (RNM, remotely monitoring bioelectric information in the human brain) has become the ultimate surveillance system. It is used by a limited number of agents in the US Intelligence Community.

The
above is a simple flowchart of Neuro-Electromagnetic Frequency Assaults
showing methods that can be perpetuated by the Police and Military
Intelligence Agencies toward
Remote Mind Control Experiments, Behavioural Manipulation and Murder.
5. [NO
HEADING IN ORIGINAL DOCUMENT]
RNM requires decoding the resonance frequency of each specific brain area. That frequency is then modulated in order to impose information in that specific brain area. The frequency to which the various brain areas respond varies from 3 Hz to 50 Hz. Only NSA Signals Intelligence modulates signals in this frequency band. (See Table 1)
This
modulated information can be put into the brain at varying intensities
from subliminal to perceptible. Each person’s brain has a unique set of
bioelectric resonance/entrainment frequencies. Sending audio
information to a person’s brain at the frequency of another person’s
auditory cortex would result in that audio information not being
perceived.
The Plaintiff learned of RNM by
being in two-way
RNM contact
with the Kinnecome group at the NSA, Ft Meade.
They used RNM 3D sound direct to the brain to harass the
Plaintiff from October 1990 to May 1991.
As of 5/91 they have had two-way RNM communications with the Plaintiff
and have used RNM to attempt to incapacitate the Plaintiff and hinder
the Plaintiff from going to the authorities about their activities
against the Plaintiff in the last 12 years. The Kinnecome
group
has about 100 persons working 24 hours a day at Ft Meade. They have
also brain-tapped persons the Plaintiff is in contact with to keep the
Plaintiff isolated. This is the first time ever that a private citizen
has been harassed with RNM and has been able to bring a lawsuit against
NSA personnel misusing this intelligence operations method.
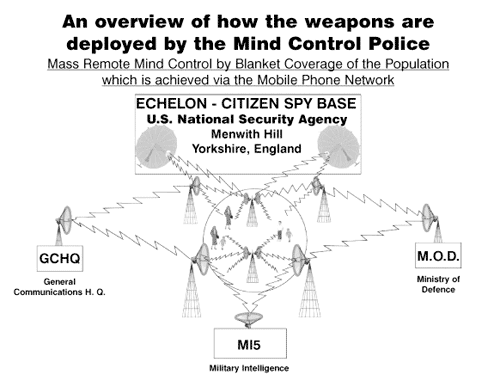
6. NSA
TECHNIQUES AND RESOURCES
Remote RNM Devices
Spotters and Walk-Bys in Metropolitan Areas
Tens of thousands of persons in each area working as spotters and neighbourhood/business place spies (sometimes unwittingly) following and checking on subjects who have been identified for covert control by NSA personnel.
Agents working out of offices can be in constant communication with spotters who are keeping track of the NSA’s thousands of subjects in public. NSA agents in remote offices can instantly identify (using~ RNM) any individual spotted in public who is in contact with surveillance subject.
Chemicals and Drugs into Residential Buildings with Hidden NSA Installed and Maintained Plastic Plumbing lines
The NSA has kits for running lines into residential tap water and air ducts of subjects for the delivery of drugs (such as sleeping gas or brainwashing-aiding drugs). This is an outgrowth of CIA pharmapsychology (psychopharmacology).
Brief Overview of Proprietary US Intelligence/Anti- Terrorist Equipment Mentioned
Fixed network of special EMF equipment that can read EEGs in human brains and identify/track individuals by using digital computers. ESB (Electrical Stimulation to the Brain) via EMF signal from the NSA Signals Intelligence is used to control subjects.
EMF equipment that gathers information from PC circuit boards by deciphering RF emissions, thereby gaining wireless modem- style entry into any personal computer in the country. All equipment hidden, all technology secret, all scientific research unreported (as in electronic warfare research). Not known to the public at all, yet complete and thorough implementation of this method of domestic intelligence has been in place since the early 1980s.
Editor’s Note : I tried ringing Mr Akwei to find out what was the out- come, if any, of his court case. He firmly but kindly told me that he could not speak about anything to do with the case over the phone and hung up. A subsequent conversation of similar length resulted in the information that he did not wish his address or phone number published with this article. So, if we hear of any developments, we’ll let you know.
|
Its
totally obvious from the above article that the US National Security
Agency is none other than a covertly run terrorist organization. |
|
RESOURCES
These publications have only been discovered since December 1991, after Plaintiff had already notified authorities (Dept of Justice, etc.) of Public Corruption by named NSA employees. When no action was taken against the NSA employees, I researched the Intelligence Community electronic surveillance technology involved and discovered the following publications.
- The
Body
Electric:
Electromagnetism and the Foundation of
Life, by Robert Becker, M.D. Monitoring neuroelectric information in
the brain ESB. (p. 265,313,318)
- Cross
currents,
by Robert
Becker. Simulating auditory
hallucinations. Remote computer tampering using RF emissions from the
logic board. (p. 70,78,105,174,210,216,220,242,299,303)
- Currents
of
Death,
by Paul
Brodeur. Driving brain
electrical activity with external EM; magnetophosphenes; Delgado. (p.
27,93)
- The
Zapping
of America,
by
Paul Brodeur. DoD EM ESB
research; simulating auditory hallucinations.
- Of
Mice, Men
and
Molecules,
by John H. Heller 1963
Bioelectricity; probing the brain with EM waves. (p, 110)
- The
Three-Pound
Universe,
by Judith Hooper. CIA EEG
research; EEGs for surveillance. (p.29,132,137)
- In
the
Palaces of
Memory,
by George Johnson. EM emissions
from the brain; the brain as an open electromagnetic circuit.
- The
Puzzle
Palace,
by James
Bamford. Signals Intelligence;
most advanced computers in the early ’sixties.
- The
US
Intelligence
Community. Glossary terms at National
Security Archives; Radiation Intelligence (information from
unintentionally emanated electromagnetic energy, excluding radioactive
sources).
- The
Search
for the
Manchurian Candidate, by John Marks.
Electrical or radio stimulation to the brain; CIA R&D in
bioelectrics. (p.227)
- Secret
Agenda,
by Jim
Hougan. National security cult
groups.
- Crimes
of
the
Intelligence
Community, by Morton Halperin.
Surreptitious entries; intelligence agents running operations against
government workers.
- War
in the
Age of
Intelligent Machines, NSA computer
supremacy, complete control of information.
- Alternate
Computers,
by
Time-Life Books. Molecule
computers.
- The
Mind,
by
Richard
Restak, M.D. EEG Systems inc.;
decoding brain EM emanations, tracking thoughts on a computer. (p. 258)
- MedTech,
by
Lawrence
Galton. Triggering events in the
brain, direct to auditory cortex signals.
- Cyborg,
by
D.S. Halacy,
Jr,
1965. Brain-to-computer link
research contracts given out by the US government.
- Psychiatry
and the
CIA:
Victims of Mind Control, by Harvey
M. Weinstein M.D. Dr. Cameron; psychic driving; ultraconceptual
communications.
- Journey
Into
Madness: The
True Story of Secret CIA Mind
Control and Medical Abuse, by Gordon Thomas, Intelligence
R&D;
Delgado; psychic driving with radio telemetry. (p. 127,276,116,168,169)
- Mind
Manipulators,
by Alan
Scheflin and Edward M. Opton.
MKULTRA brain research for information-gathering.
- The
Brain
Changers,
by Maya
Pines. Listening to brain EM
emissions. (p.19)
- Modern
Bioelectricity.
Inducing audio in the brain with EM
waves; DoD cover-up; EM wave ESB; remote EEGs
- Magnetic Stimulation in Clinical Neurophysiology, by Sudhansu Chokroverty. Magnetophosphenes; images direct to the visual cortex.
- The
Mind of
Man,
by Nigel
Calder. US intelligence brain
research.
- Neuroelectric Society Conference, 1971. Audio direct to the brain with EM waves; 2-way remote EEGs.
- Brain Control, by Elliot S. Valenstein. ESB., control of individuals.
- Towards
Century 21, by C.S.
Wallia. Brain Stimulation for
direct-to-brain communications (p21)
- Mind
Wars,
by
Ron McRae
(associate of Jack Anderson).
Research into brain-to-brain electronic communications., remote neural
EM detection (PP. 62 106, 136).
- Mind
Tools,
by
Rudy Rucker.
Brain tapping; communications
with varying biomagnetic fields (p82).
- US
News
and
World report,
January 2nd 1984. EM wave brain
stimulation; intelligence community hi-tech (p38).
- Ear
Magazine. Article on extremely low frequencies radio
emissions in the natural environment; radio emissions from the human
body.
- City
Paper, Washington DC January 17, 1992. Article FCC
and NSA "complete radio spectrum" listening posts.
- Frontiers
in Science, by Edward Hutchings Jr 1958 (p48).
- Beyond
Bio Feedback, by Elmer and Alyce Green, 1977 (p118)
- The
Body Quantum, by Fred Alan Wolf
- Cloning;
A Biologist Reports, by Robert Gillmore
McKinnell. Ethical review of cloning humans.
- Hoovers’
FBI,
by
Former agent William Turner.
Routines of
electronic surveillance work. (p280).
- July 20th
2019,
by Arthur C. Clarke LIDA;
Neurophonics;
Brain-computer link.
- MegaBrain,
by Michael Hutchison. Brain stimulation with EM
waves; CIA research and information control. (pp.107,108,117,120,123).
- The
Cult of Information, by Theodore Rosnak, 1986. NSA
Directive #145; personal files in computers; computer automated
telephone tapping.
- The
Body Shop, 1986 implantation of an electrode array on
the visual cortex for video direct to the brain; other 1960’s research
into electronically triggering Phosphenes in the brain, thus bypassing
the eyes.
- Evoked Potentials, by David Regan. Decoding neuroelectric information in the brain.
Flow-charts of
probable original
circuits of Neurophone
Detecting emf fields in humans for surveillance
Signals Intelligence implemented and kept this technology secret in the same manner as other electronic warfare programs of the U.S. government. The NSA monitors available information about this technology and withholds scientific research from the public. There are also international intelligence agency agreements to keep this technology secret. The NSA has proprietary electronic equipment that analyzes electrical activity in humans from a distance. NSA computer-generated brain mapping can continuously monitor all the electrical activity in die brain continuously. The NSA records aid decodes individual brain maps (of hundreds of thousands of persons) for national security purposes.
EMF Brain Stimulation is also secretly used by the military for Brain-to-computer link. (In military fighter aircraft, for example.) For electronic surveillance purposes electrical activity in the speech center of the brain can be translated into the subject's verbal thoughts. RNM can send encoded signals to the brain's auditory cortex thus allowing audio communication direct to the brain (bypassing the ears). NSA operatives can use this to covertly debilitate subjects by simulating auditory hallucinations characteristic of paranoid schizophrenia. Without any contact with the subject, Remote Neural Monitoring can map out electrical activity from the visual cortex of a subject's brain and show images from the subject's brain on a video monitor. NSA operatives see what the surveillance subject's eyes are seeing. Visual memory can also be seen. RNM can send images direct to the visual cortex. bypassing the eyes and optic nerves. NSA operatives can use this to surreptitiously put images in a surveillance subject's brain while they are in R.E.M. sleep for brain-programming purposes.
Neuronal activity in the brain creates a shifting electrical pattern that has a shifting magnetic flux. This magnetic flux puts out a constant 30-50 hz, .5 milliwatt electromagnetic (EMF) wave.
Contained in the electromagnetic emission from the brain are spikes and patterns called evoked potentials. Every thought, reaction, motor command, auditory event, and visual image in the brain has a corresponding "evoked potential" or set of "evoked potentials". The EMF emission from the brain can be decoded into the current thoughts, images and sounds in the subject's brain. NSA SigInt uses EMF-transmitted Brain Stimulation as a communications system to transmit information (as well as nervous system messages) to intelligence agents and also to transmit to the brains of covert operations subjects (on a non-perceptible level).
Two-Way Electronic Brain Link has become the ultimate communications system for CIA/NSA personnel. Remote Neural Monitoring (RNM, remotely monitoring bioelectric information in the human brain) has become the ultimate surveillance system. It is used by a limited number of agents in the U.S. Intelligence Community.
RNM requires decoding the resonance frequency of each specific brain area. That frequency is then modulated in order to impose information in That specific brain area. The frequency to which the various brain areas respond varies from 3 Hz to 50Hz. Only NSA Signals Intelligence modulates signals in this frequency band.
Motor Control Cortex 10 HZ Motor Impulse Co-ordination
Auditory Cortex 15 HZ Sound which bypasses the ears
Visual Cortex 25 HZ Images in the brain, bypassing the eyes
Somatosensory Cortex 09 HZ Phantom Touch Sense
Thought Center 20 HZ Imposed Subconscious Thoughts
This modulated information can be put into the brain at varying intensities from subliminal to perceptible. Each person's brain has a unique set of bioelectric resonance/entrainment frequencies. Sending audio information to a person's brain at the frequency of another person's auditory cortex would result in that audio information not being perceived.
The Plaintiff learned of RNM by being in two-way RNM contact with the Kinnecome group at the NSA, Ft. Meade. They used RNM 3D sound direct to the brain to harass the Plaintiff from10/90 to 5/91. As of 5/91 they have had two-way RNM communications with the Plaintiff and have used RNM to attempt to incapacitate the Plaintiff and hinder the Plaintiff from going to authorities about their activities against the Plaintiff in the last twelve years.
(Any way it is to be strictly considered that - for the time being - these quotes are just ALLEGATIONS and have not been proven.)
PDF files
STOA-Parlamento.Europeo
Sirus.Project
U.S._intellingence_and_security
Possible_influence-on_subject_FOIA.pdf
LEGGE.HR3200.pdf
Armi ad Energia diretta
Caso Suda: file originale
suda.fotodoc
LarsonReport-Edit
Nota: i file in pdf potranno essere duplicati o riprodotti su supporti elettronici, cartacei o di qualsiasi altro tipo e distribuiti liberamente, a DUE CONDIZIONI.
2) L'eventuale distribuzione dei duplicati, qualsiasi sia il supporto, dovrà essere fatta esclusivamente a titolo GRATUITO.
2) Any circulation of the duplicates, whatever the support, must be FREE OF CHARGE.
Quando la cartella clinica è terapeutica.Dare ai ricordi una seconda vita?
Consapevolezza e memoria
Medicina: scienza applicata e multidisciplinare: Emozioni, istinti, ricordi, contraddizioni
libri scaricabili in rete / pdf of complete books
Infanzia:un-mestiere-difficilissimo Copertina libro Infanzi
Consapevolezza e Memoria
SIrUS Project
STOA: Parlamento Europeo
Le Armi a Energia Diretta
Cinque libri legati da un unico filo
Il Prezzo del Potere
Dal sito dell'Ingegner Giuseppe Muratori: 'NUOVO' WORLD INTELLIGENCE FOUNDATION
Testimonianze di un ingegnere informatico / Testimony of an informatic
Links e citazioni su segnali di pericolo
...altre sopraffazioni e violazioni
Segnalazioni di Allarme:Internazionali
Aggressioni pseudo-misteriose contro bersagli biologici
Fake-mysteries on biological targets
Opinioni o peggio: accuse?
Opinion or accusation?
L'aggiornamento dell'effettiva attività dei link si svolge in modo continuativo
As every other file of this site, the review of links does continually checked.
Online Broken Link Checker
MONITORAGGIO dei link afferenti al sito - e alle sue singole pagine
To WATCH the outbound links toward site - and its inner pages.
2022 Copyrights | aisjca-mft.org










